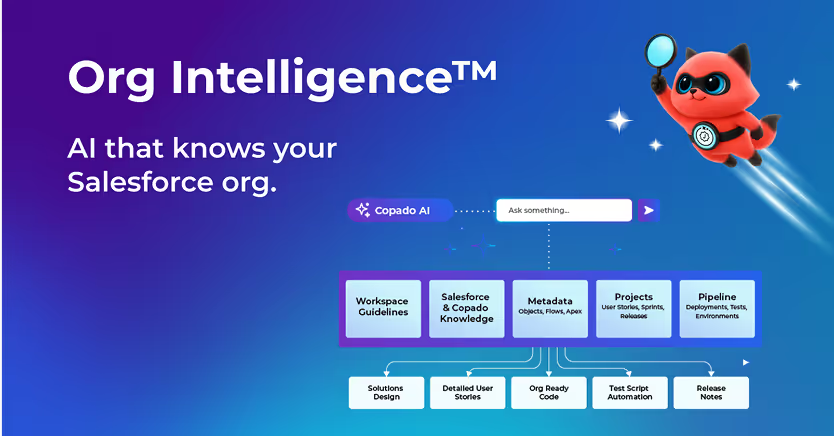
Get Free Access to Copado Org Intelligence™
Smarter DevOps is just a click away. Discover your architecture, automations, and risks instantly.


Get Free Access to Copado Org Intelligence™
Smarter DevOps is just a click away. Discover your architecture, automations, and risks instantly.
Learn Copado on the world’s largest DevOps community
Where’s Copado headed next? See our upcoming schedule
Articles full of tips & tactics written by Copado users
Watch Copado capabilities in action with our video hub
Thought leadership and key info from industry experts
Ready for a DevOps deep dive? Read our latest research
Explore our DevOps resource library.


Get Free Access to Copado Org Intelligence™
Smarter DevOps is just a click away. Discover your architecture, automations, and risks instantly.
Learn Copado on the world’s largest DevOps community
DevOps terms, definitions & step-by-step instructions
Accelerate time-to-value with expert guidance
Enterprise-Grade security for Salesforce development
Optimize your DevOps ecosystem with flexible, pre-built integrations
Copado welcomes feedback from security researchers and the general public to help improve our security. If you believe you have discovered a vulnerability, privacy issue, exposed data, or other security issues in any of our assets, we want to hear from you. This policy outlines steps for reporting vulnerabilities to us, what we expect, what you can expect from us.
This policy applies to any digital assets owned, operated, or maintained by Copado.
Assets or other equipment not owned by parties participating in this policy.
Vulnerabilities discovered or suspected in out-of-scope systems should be reported to the appropriate vendor or applicable authority.
When working with us, according to this policy, you can expect us to:
In participating in our vulnerability disclosure program in good faith, we ask that you:
Please report security issues via mailto://security@copado.com, providing all relevant information. The more details you provide, the easier it will be for us to triage and fix the issue.
When conducting vulnerability research, according to this policy, we consider this research conducted under this policy to be:
You are expected, as always, to comply with all applicable laws. If legal action is initiated by a third party against you and you have complied with this policy, we will take steps to make it known that your actions were conducted in compliance with this policy.
If at any time you have concerns or are uncertain whether your security research is consistent with this policy, please submit a report through one of our Official Channels before going any further.
Note that the Safe Harbor applies only to legal claims under the control of the organization participating in this policy, and that the policy does not bind independent third parties.